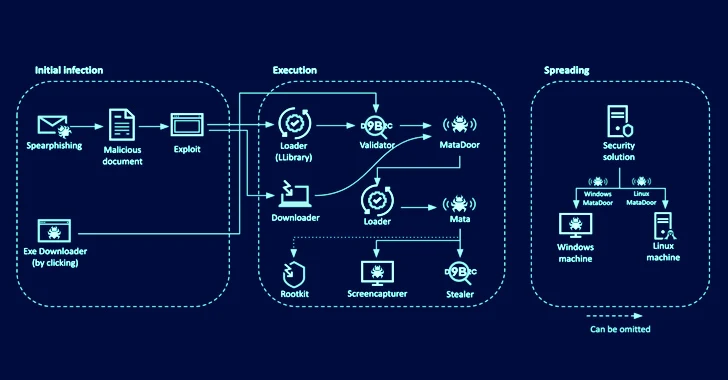
Iran-Linked MuddyWater Hackers Target U.S. Networks With New Dindoor Backdoor

New research from Broadcom's Symantec and Carbon Black Threat Hunter Team has discovered evidence of an Iranian hacking group embedding itself in several U.S. companies' networks, including banks, airports, non-profit, and the Israeli arm of a software company. The activity has been attributed to a state-sponsored hacking group called MuddyWater (aka Seedworm). It's affiliated with the Iranian Ministry of Intelligence and Security (MOIS). The campaign is assessed to have begun in early February, with recent activity detected following U.S. and Israeli military strikes on Iran. "The software company is a supplier to the defense and aerospace industries, among others, and has a presence in Israel, with the company's Israel operation seeming to be the target in this activity," the security vendor said in a report shared with The Hacker News. The attacks targeting the software company, as well as a U.S. bank and a Canadian non-profit, have been found to pav...