Dark Power Ransomware on the Ascent – A Technical Insight into 2023’s Latest Ransomware Strain
In early February 2023, a new ransomware strain quietly made its way up the ranks. Earmarked Dark Power, the NIM-written ransomware leverages an advanced block cipher technique to bypass detection, stop system-critical services, and, finally to encrypt the victim’s file. In this article, we are going to deep-dive into Dark Power Ransomware, by taking a closer look at TTPs (i.e., Tactics, Techniques, and Procedures), post-infection action(s) on object, targeting discrimination (or the lack of), and more.
Dissecting the Dark Power Ransomware
From a historical perspective, the Dark Power ransomware’s origins can be traced back to early 2020 when it was just a small blip on the security specialists’ radar. The analysis performed on the sample revealed a very crude, yet effective file encryption and ransoming mechanism – Dark Power’s first iteration would have employed an encryption technique that randomly generated a (victim) unique 64-character ASCII string, later to be used in order to derive the decryption key. In addition, the attacker would also have dropped a pdf ransom note with instructions on how to retrieve data (i.e., in all cases, the victim received an XMR wallet handle and a 72-hour payment window).
Even at this point in time, the APT remains unknown, although intel points out to a global operation; some of the earliest reports on the ransomware tied the APT to multiple hits across the world, specifically targeting business entities from various sectors, including education, healthcare, manufacturing, and food production. Instances bearing Dark Power’s mark have been identified in the United States, Peru, Turkey, France, Israel, Egypt, Algeria, and the Czech Republic.
Fast-forward to 2023, Dark Power is yet again on the prowl, and more virulent than ever. Recent intel reveals that this particular ransomware has compromised at least 10 businesses since its resurgence in early February.
Technical Analysis
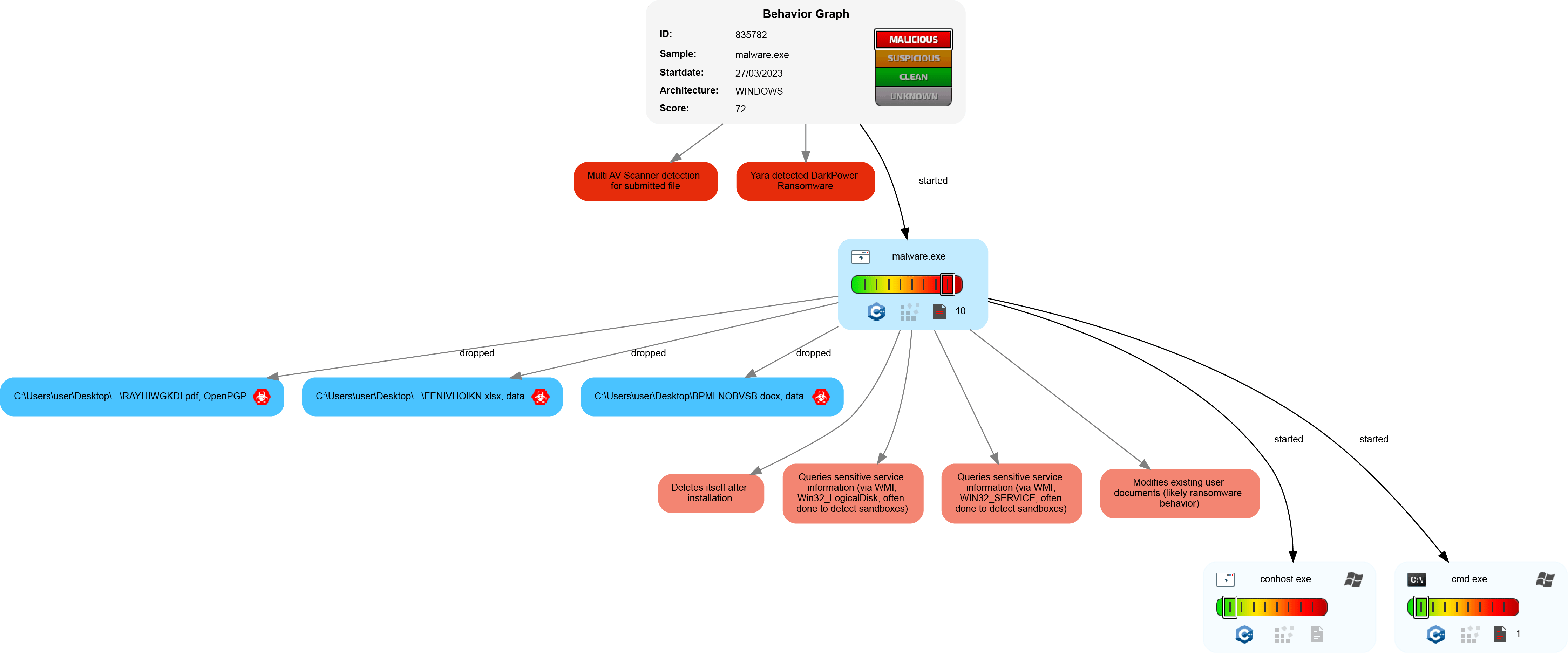
Obtained Dark Power sample indicates the evil code has undergone a major overhaul, especially in areas such as obfuscation, data encryption, execution, and, of course, extortion.
The flow can be reviewed below.
Photo courtesy of MalwareBazaar
Infiltration
By all accounts, the APT employs non-discriminative evil code dissemination methods. With limited information on the topic, we can surmise that Dark Power is more than likely delivered by phishing emails. Vulnerability exploitation could also qualify as a feasible point of entry.
Execution & Action(s) on Object
Upon infiltration, the Dark Power ransomware initiates the following workflow – encryption key initiation, binary string encryption, process & service termination, creating file & folder exclusions, and dropping the ransom note.
PRIMING THE ENCRYPTION KEY. BINARY STRING ENCRYPTION.
The first post-execution action on target performed by Dark Power is the priming of the encryption key. By leveraging NIM’s Nimcrypto library, the malware is able to create a unique data encryption key, thereby hindering reverse-engineering efforts (i.e., the victim is unable to use open-source tools in order to derive the decryption key). The process begins with Dark Power generating a distinctive and arbitrary 64-character AES ASCII string. Once the string is generated, it will then be used to initialize the AES Counter (CTR) encryption algorithm. This operation serves two purposes:
- Hinders decryption efforts. CTR initialized by a randomized AES ASCII string makes it impossible for the defender to retrieve encrypted files using a generic decryption tool.
- Prevents fingerprinting. Defenders will be unable to design a general detection rule for the ransomware.
Finally, the malware will decode the encrypted string by leveraging a fixed key (most commonly an SHA-256 hash of the hard-coded key). An extra challenge is also added – although the initialization vector is hardcoded in Dark Power’s binary, each decryption instance calls out a different initialization vector.
STOPPING SERVICES AND PROCESSES.
Once the encryption phase is completed, the malware will proceed to stop essential services and processes. Our analysis revealed no atypicality in Dark Power’s process-stopping and Volume Shadow Service service termination behavior – the ransomware first stops the Volume Shadow Service (VSS). This prevents the defender from restoring encrypted files from the backup.
Furthermore, with the VSS disabled, the ransomware will be free to encrypt files that, under normal circumstances (i.e., normal OS behavior), would be locked or otherwise inaccessible. Dark Power also stops system processes that could impede the malicious encryption operation – this includes ancillary backup services and anti-malware solutions.
The full list of processes stopped by the ransomware can be found below. It is important to note that Dark Power’s (process) kill list is hardcoded in the malware’s binary.
• taskmgr.exe
• agntsvc.exe
• synctime.exe
• encsvc.exe
• mspub.exe
• infopath.exe
• powerpnt.exe
• onenote.exe
• mydesktopservice.exe
• ocssd.exe
• winword.exe
• firefox.exe
• steam.exe
• thebat.exe
• oracle.exe
• isqlplussvc.exe
• excel.exe
• sqbcoreservice.exe
• outlook.exe
• mydesktopqos.exe
• dbeng50.exe
• sql.exe
• ocautoupds.exe
• tbirdconfig.exe
• ocomm.exe
• thunderbird.exe
• msaccess.exe
• visio.exe
• dbsnmp.exe
• wordpad.exe
• xfssvccon.exes
FILE EXCLUSIONS
Upon stopping VSS and killing associated processes, the ransomware will begin creating exclusions in order to prepare for the last step of the operation which is dropping the ransom note. This step ensures that the machine retains functionality since the victim is required to perform certain operations in order to reimburse the attacker. The list of exclusions (i.e., extensions, files, and folders) can be found below.
- .lib
- .theme
- .dll
- .bin
- .ocx
- .search-ms
- .msi
- .hta
- .mod
- .rom
- .dat
- .sys
- .deskthemepack
- .ics
- .prf
- .ini
- .wpx
- .nomedia
- .com
- .themepack
- .regtrans-ms
- .cpl
- .msu
- .hlp
- .msstyles
- .ps1
- .adv
- .rtp
- .spl
- .lnk
- .log2
- .msc
- .msp
- .nls
- .icns
- .log1
- .scr
- .idx
- .cab
- .mpa
- .blf
- .bat
- .ani
- .exe
- .drv
- .ldf
- .key
- .386
- .diagpkg
- .cur
- .lock
- .ico
- .diagcfg
- .icl
- .diagcab
- .cmd
- .shs
- inf
- bin
- ntldr
- dat.log
- dat
- db
- ini
- ini
- bak
- db
- ini
- program files
- $recycle.bin
- tor browser
- appdata
- old
- windows
- mozilla
- programdata
- intel
- $windows.~ws
- system volume information
- perflogs
- application data
- program files (x86)
- msocache
- $windows.~bt
- boot
CLEARING LOGS & CONSOLE. DROPPING THE RANSOM NOTE.
After creating file & folder exclusions, the ransomware will typically go to sleep for roughly 30 seconds before attempting to clear Windows logs and the console. In all observed instances, Dark Power would either use the /c cls argument in Windows command to clear the console or leveraged similar arguments (i.e., ClearEventLog() or Select * from Win32_NTEventLogFile) in WMI to perform the same tasks. This phase is essential, as it hampers any and every forensics effort on the defender’s side.
With the logs and console cleared, Dark Power will continue to enumerate and encrypt before dropping the .pdf ransom note. The document is usually placed on the victim’s desktop and contains some distinctive elements: the ransom (i.e., in or around $10,000), Monero (XMR) blockchain address, an onion link to a claimed victims dark webpage, and a qTox handle for instant messaging.
Annex
VirusTotal info:
- MD5: df134a54ae5dca7963e49d97dd104660
- SHA-1: 9bddcce91756469051f2385ef36ba8171d99686d
- SHA-256: 11ddebd9b22a3a21be11908feda0ea1e1aa97bc67b2dfefe766fcea467367394
- File type :Win32 EXE executable, windows win32, peexe, PE32+ executable for MS Windows (console) Mono/.Net assembly
COMPOSITION
- Microsoft Visual C++ compiled executable (generic) (41.1%)
- Win64 Executable (generic) (26.1%)
- Win16 NE executable (generic) (12.5%)
- Windows Icons Library (generic) (5.1%)
- OS/2 Executable (generic) (5%)
- File size 1.26 MB (1323422 bytes)
Header Analysis (Filescan.io)
ImageBase:0x140000000
- EntrypointName: .text
- EntrypointEntropy: 6.2
- EntrypointVA: 0x140001125
CALLBACKS:
- Va:0x4002aec0
- Va:0x1
- Va:0x4002af7f
- Va:0x1
- Va:0x40034328
- Va:0x1
- CrcInFile:0x14a3df
- CrcActual:0x14a3df
- LinkerVersionMajor:2
- LinkerVersionMinor:36
COMPILERFLAGS:
- IsASLR:true
- IsNXCOMPAT:true
- IsSEH:false
- IsCFG:false
- IsGS: false
- PointerToSymbolTable:0x10cc00
- NumberOfSymbols:0x1972
Behavior Analysis (via Dr. Web vxCube)
- Using the Windows Management Instrumentation requests
- Running batch commands
- Creating a file
- Changing a file
- Reading critical registry keys
- Moving a recently created file
- Possible injection into a system process
- Stealing user-critical data
- Moving the original file
- Bypassing of proactive protection methods using Windows Management Instrumentation (WMI)
- Forced shutdown of a browser
- Encrypting user’s files
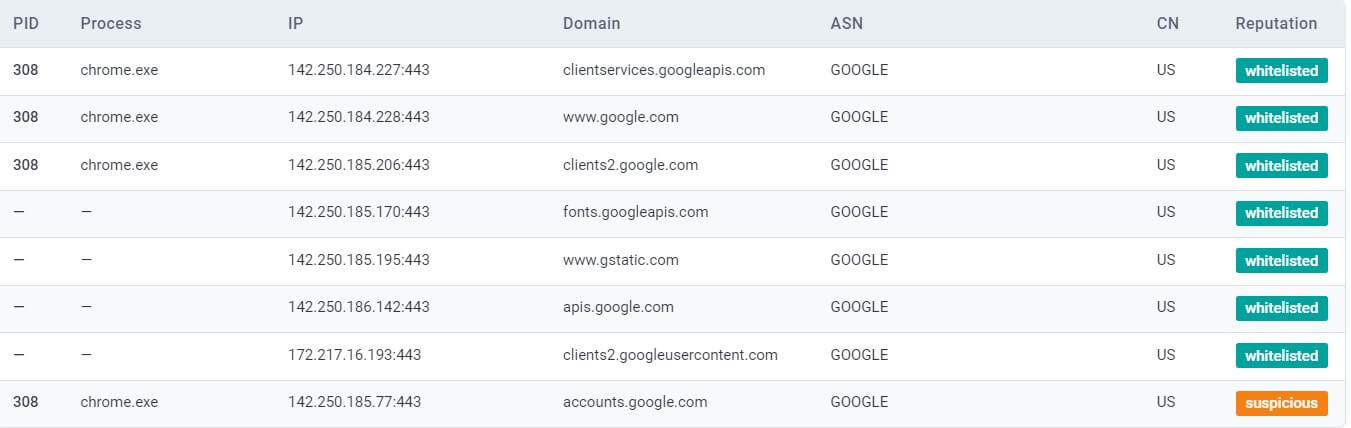
Established connections (via Anyrun)
Conclusion
On the defender’s side, extra precautions are not necessary – avoid downloading content from suspicious websites, don’t open email attachments from senders that are outside of your emailing list, and don’t follow any links that might be enclosed in these emails. On top of that, ensure that your AV’s up to date, and consider deploying a ransomware encryption protection solution.
EK




Comments
Post a Comment