Phishing attacks: defending your organisation
How to defend your organization from email phishing attacks.
Introduction to Phishing
Phishing attacks: defending your organization provides a multi-layered set of mitigations to improve your organization's resilience against phishing attacks, whilst minimizing disruption to user productivity. The defenses suggested in this guidance are also useful against other types of cyber attack, and will help your organization become more resilient overall.
- This guidance is aimed at technology, operations or security staff responsible for designing and implementing defenses for medium to large organizations. This includes staff responsible for phishing training.
- Staff within smaller organizations will also find this guidance useful, but should refer to the NCSC's Small Business Guide beforehand.
- This guidance concludes with a real-world example that illustrates how a multi-layered approach prevented a phishing attack from damaging a major financial-sector organization.
Note: The mitigations included in this guidance require a combination of technological, process, and people-based approaches. They must be considered as a whole for your defenses to be really effective. For example, if you want to encourage people to report suspicious emails, then you need to back that up with a technical means of doing so, and a process behind it that will provide timely feedback on the email they submitted.
What is phishing?
Phishing is when attackers attempt to trick users into doing 'the wrong thing', such as clicking a bad link that will download malware, or direct them to a dodgy website.
Phishing can be conducted via a text message, social media, or by phone, but the term 'phishing' is mainly used to describe attacks that arrive by email. Phishing emails can reach millions of users directly, and hide amongst the huge number of benign emails that busy users receive. Attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Phishing emails can hit an organization of any size and type. You might get caught up in a mass campaign (where the attacker is just looking to collect some new passwords or make some easy money), or it could be the first step in a targeted attack against your company, where the aim could be something much more specific, like the theft of sensitive data. In a targeted campaign, the attacker may use information about your employees or company to make their messages even more persuasive and realistic. This is usually referred to as spear phishing.
Every organization can play a part
The mitigations described here are mostly focused on preventing the impact of phishing attacks within your organization, but they include some measures that will help protect the whole of the UK. For example, setting up DMARC stops phishers from spoofing your domain (that is, making their emails look like they come from your organization). There are numerous benefits in doing this:
- Your own company's genuine emails are more likely to reach the recipients' inboxes, rather than getting filtered out as spam.
- From a reputational aspect, no organization wants their name becoming synonymous with scams and fraud.
- The wider community will also benefit if your contacts (such as suppliers, partners and customers) are encouraged to register their details with DMARC. This can give you much greater assurance that the email asking for information (or money) actually comes from where you think.

The NCSC are encouraging organizations to lead by example and set up DMARC, and then start asking their contacts to do the same. It's in everyone's interest to promote widespread adoption, as the more organizations that take part, the harder it is for the phishers to succeed.
Phishing defences: why you need a multi-layered approach
Typical defenses against phishing often rely exclusively on users being able to spot phishing emails. This approach will only have limited success. Instead, you should widen your defenses to include more technical measures. This will improve your resilience against phishing attacks without disrupting the productivity of your users. You'll have multiple opportunities to detect a phishing attack, and then stop it before it causes harm. You also acknowledge that some attacks will get through, as this will help you plan for incidents, and minimize the damage caused.
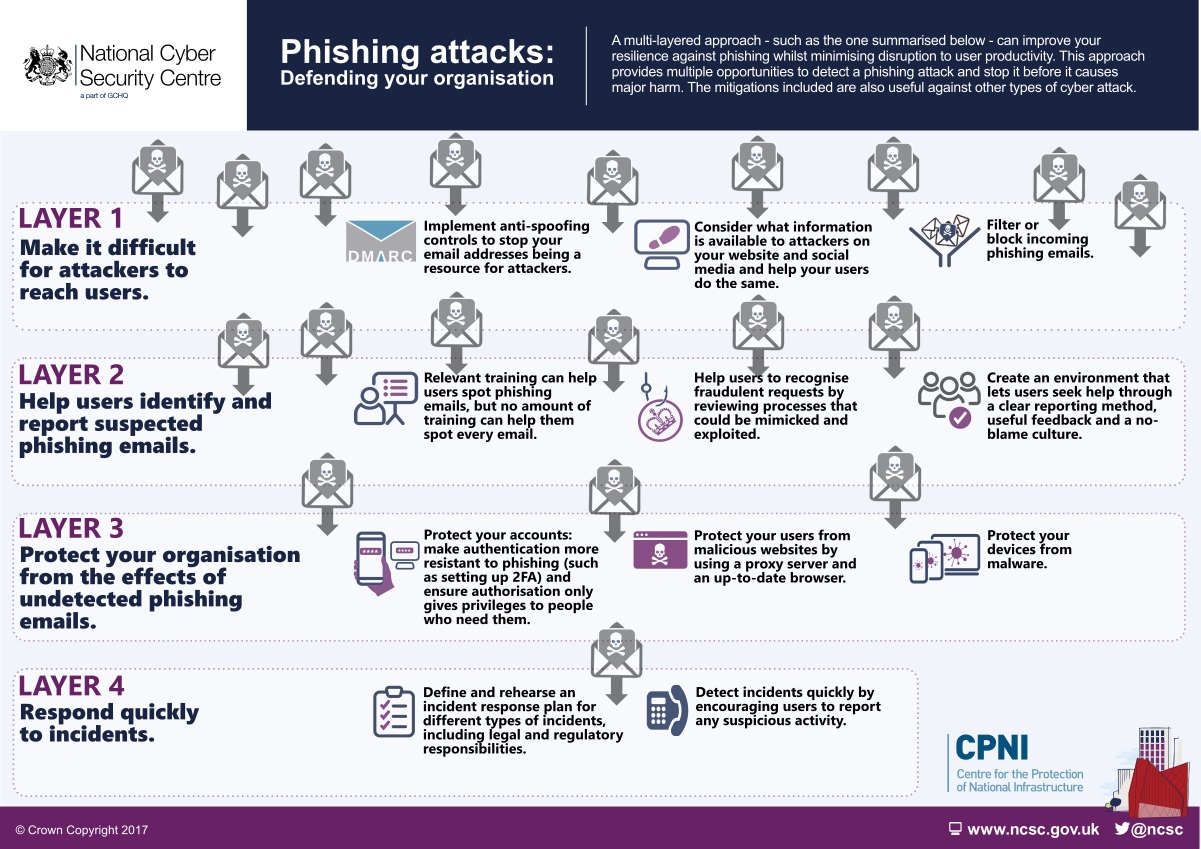
This guidance splits the mitigations into four layers on which you can build your defenses:
- Make it difficult for attackers to reach your users
- Help users identify and report suspected phishing emails
- Protect your organization from the effects of undetected phishing emails
- Respond quickly to incidents
Some of the suggested mitigations may not be feasible within the context of your organization. If you can't implement all of them, try to address at least some of the mitigations from within each of the layers. The mitigations within each layer are summarized in the following infographic.
Summary of multi-layered approach to phishing defences
Four layers of mitigation
Layer 1: Make it difficult for attackers to reach your users
Layer 2: Help users identify and report suspected phishing emails
Layer 3: Protect your organization from the effects of undetected phishing emails
Layer 4: Respond quickly to incidents
Case study: how multi-layered phishing mitigations defended against Dried malware
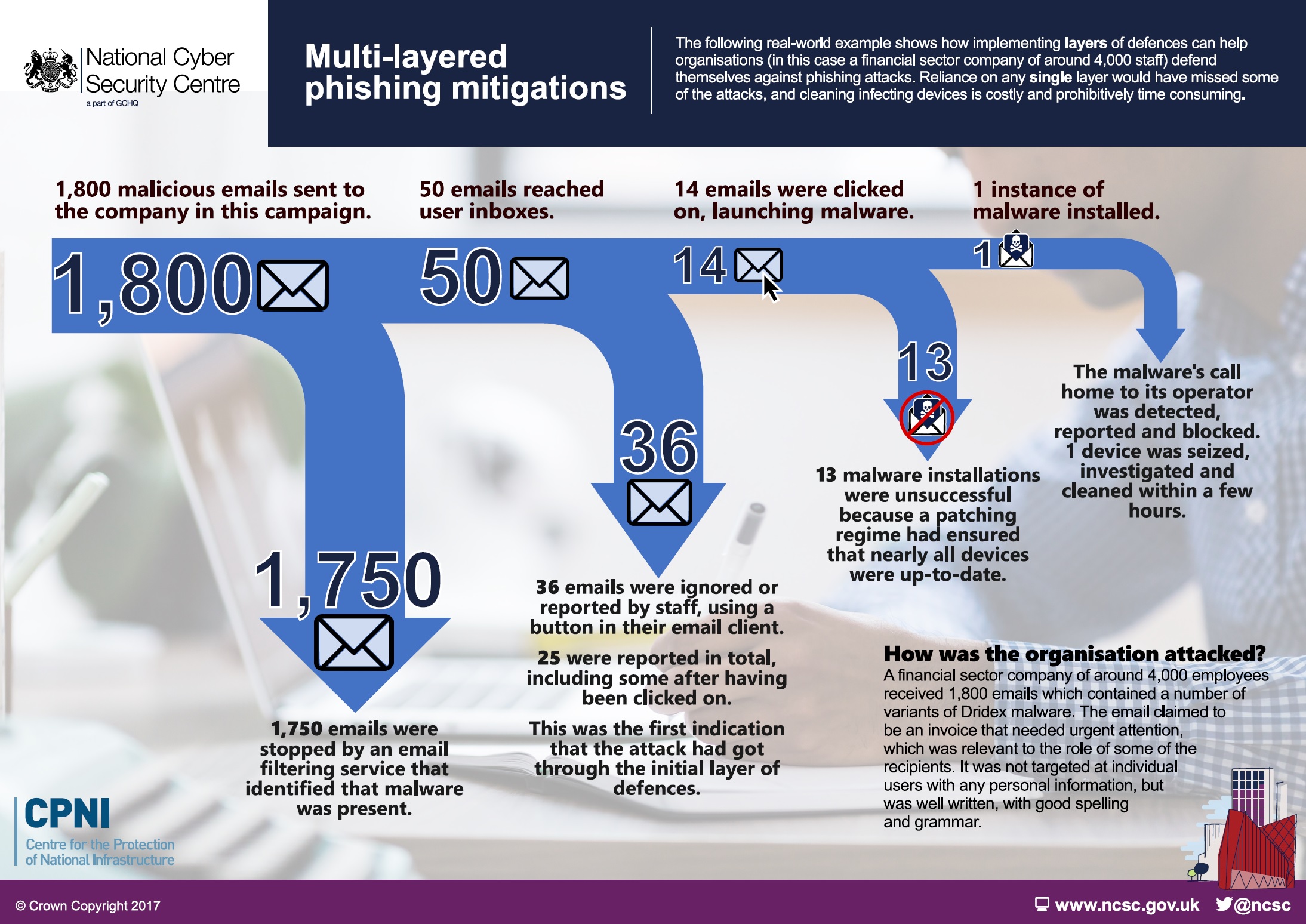
The following real-world example illustrates how a company in the financial sector used effective layered mitigations to defend against phishing attacks. Reliance on any single layer would have missed some of the attacks, or in the case of relying on cleaning up quickly afterwards, be very costly and prohibitively time consuming.
The company, which has around 4,000 employees, received 1,800 emails containing a number of variants of Dried malware. The email claimed to be an invoice that needed urgent attention, which was relevant to the role of some of the recipients. It was not targeted at individual users with any personal information, but was well written, with good spelling and grammar.
 Download the phishing mitigations case study below (pdf)
Download the phishing mitigations case study below (pdf)
Summary of the phishing attack:
- 1,800 emails were sent to the organization by this campaign
- 1,750 were stopped by an email filtering service that identified that malware was present.
- 1,750 were stopped by an email filtering service that identified that malware was present.
- This left 50 emails that reached user inboxes.
- Of these, 36 were either ignored by users, or reported using a button in their email client. 25 were reported in total, including some post click; this was the first indication that the attack had got through the initial layer of defenses.
- Of these, 36 were either ignored by users, or reported using a button in their email client. 25 were reported in total, including some post click; this was the first indication that the attack had got through the initial layer of defenses.
- This left 14 emails that were clicked-on, which launched the malware.
- 13 instances of the malware failed to launch as intended due to devices being up-to-date.
- 13 instances of the malware failed to launch as intended due to devices being up-to-date.
- 1 instance of malware was installed.
- The malware's call home to its operator was detected, reported and blocked.
- 1 device was seized, investigated and cleaned in a few hours.
- Reference: https://www.ncsc.gov.uk/guidance/phishing





Comments
Post a Comment