Real Enough to Fool You: The Evolution of Deepfakes
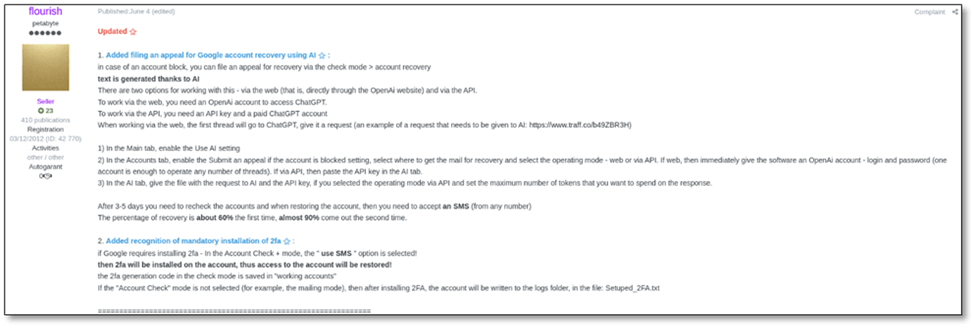
Not long ago, deepfakes were digital curiosities – convincing to some, glitchy to most, and often more meme than menace. Fast forward to 2025, and they’ve become fully weaponized, commercially available, and dangerously scalable. What began as clever video edits has become a self-operating engine for social engineering, fraud, and identity theft.
According to Check Point Research’s AI Security Report 2025, we’ve reached a pivotal moment: deepfake technology now spans from basic offline generation to fully autonomous, real-time impersonation engines, capable of deceiving even seasoned professionals.
Deepfakes by the Numbers: Where We Stand
Over $35 million in fraud losses have been attributed to deepfake video scams in just two high-profile cases in the UK and Canada.
AI-driven voice deepfakes are now used regularly in sextortion, CEO impersonation, and hostage scams—one case in Italy saw criminals impersonate the Minister of Defense in a live call to extort high-profile contacts.
AI-enhanced telephony systems, priced at around $20,000, can now impersonate any voice in any language across multiple conversations simultaneously—no human operator required.
These systems are available right now on dark web forums and Telegram marketplaces.
Automation Has Changed the Game
The report introduces a “Deepfake Maturity Spectrum” (page 12) highlighting how generative AI has evolved from static content creation and will soon reach autonomous agents that conduct live, video conversations with unsuspecting targets. Let’s break it down:
| Generation Type | Technology Level | Use Case Example |
| Offline | Pre-rendered scripts and media | Phishing emails, impersonation videos |
| Real-Time | Live face-swapping, voice modulation | Fake video calls with CFOs, emergency fund scams |
| Autonomous | Interactive AI agents handling live chats | Real-time impersonation across multiple platforms simultaneously |
Today’s most advanced malicious tools are powered by LLMs like DeepSeek and Gemini, and driven by customized models like WormGPT and GhostGPT. These tools not only generate content—they hold dynamic conversations, analyze victim responses, and adapt tone and language on the fly.
The Criminal Toolkit: Democratized and Commodified
Gone are the days when advanced deception required elite cyber crime syndicates. Now:
- Voice cloning tools like ElevenLabs can generate a convincing voice in under 10 minutes from short audio samples.
- Face-swapping plugins for live video are available in underground marketplaces starting at a few hundred dollars.
- One AI-driven phishing suite, GoMailPro, was openly advertised on Telegram for $500/month, with built-in ChatGPT support.
- Business email compromise kits, like the “Business Invoice Swapper,” automatically scan inboxes and alter invoice details using AI—scaling fraud with near-zero manual input.
Cyber crime has effectively outsourced creativity to machines. Now, even low-skilled attackers can launch sophisticated operations.
What Happens When Real and Fake Blur?
The FBI has already warned that AI-generated images, videos, and voices are undermining traditional forms of trust and verification. From job interview scams involving real-time face swaps to fake conference calls impersonating executives, the line between digital fiction and fact is evaporating.
Security teams can no longer rely on gut instinct or visual checks:
- Real and AI-generated voices are now indistinguishable.
- Audio deepfakes are already a go-to method for large-scale social engineering campaigns.
These aren’t theoretical risks—they’re already embedded in real-world attacks.
Proactive Defense Against a Self-Running Threat
To help organizations stay protected, Check Point’s solutions offer complete protection across file types, operating systems, and attack surfaces and proactively:
- Detect and block AI-generated threats like fake media files and phishing payloads
- Isolate suspicious behavior linked to autonomous AI agents
- Neutralize malware embedded in deepfake files or used to deliver them
Coupled with user awareness and zero trust principles, these solutions form a comprehensive shield against an adversary that never sleeps.
Deepfakes Aren’t the Future. They’re Here.
Organizations can no longer afford to view deepfakes as a fringe novelty. As the AI Security Report 2025 shows, deepfakes have become self-generating, market-driven, and operationalized. Their ability to scale, deceive, and adapt in real-time marks a shift in the balance of cyber power.
Reference: https://blog.checkpoint.com/




Comments
Post a Comment